April 2, 2021 | 8 minute read
While it would be counterproductive to curtail the process of finding qualified (technical) cybersecurity workers to be considered for a specific job role by diverting any attention away, we want to add to the conversation by also embracing and advocating for other, essential job roles within cybersecurity that don’t necessarily imply technical experience. Across the cyber ecosystem, there are different roles that require different skills, and that includes non-technical roles that are just as important to the functioning of the ecosystem, and depend more on competencies, or soft skills, such as leadership, interpersonal, operational, and more. These are skills that could have previously been acquired through a number of different backgrounds and work experiences. To fill the roles like the ones we describe later in this post, hiring managers and recruiters would be wise to cast a wide net. By welcoming and fostering a variety of different backgrounds and experiences into the cybersecurity industry, diversity becomes the foundation of stability, unity, harmony, and achieving a clearly defined objective.
Diversity in Experience, Sans Niche Skills
It may or may not surprise you to know, not everyone who enters the cybersecurity workforce needs the skills required to identify and record security flaws and breaches, or perform penetration tests. Diversity in the workplace not only refers to gender, racial, ethnic, orientation, cultural, neuro and social aspects, but it also points to “lived experiences”, and thus differences in abilities and perspectives. For the purpose of this blog post, we are focusing on diversity in lived experience, with regards to non-technical workers as necessities for building a stronger cybersecurity workforce.
“There’s a perception in the industry that cybersecurity is complex and requires niche skills. Actually, the skills needed for cybersecurity are used in all interaction between humans and technology and between technology and technology.”
Class, age, education, geography, traumas, achievements, beliefs, and upbringings are all contributing factors to lived experience. The things an individual has “lived through” amounts to much more than the preconceived biases and constructs that previous hiring practices, as well as societal and workplace culture, have placed on job-seekers. In a recent TechBeacon blog post, Accenture Security’s global Growth and Strategy Lead, Neha Joshi, puts it simply, “There’s a perception in the industry that cybersecurity is complex and requires niche skills. Actually, the skills needed for cybersecurity are used in all interaction between humans and technology and between technology and technology.” It is notions like this that might inspire an elementary school teacher to start learning more about technology, with a career goal of taking on a managerial position at an IT company, or a military veteran seeking a role as a security product manager, which relies heavily on communication skills.
“The key is not a technical background, but your willingness and desire to learn how technology works and to never stop playing.”
Coupling a variety of lived experiences along with innate curiosity, affords growth across the cyber ecosystem. “The key is not a technical background, but your willingness and desire to learn how technology works and to never stop playing.” (SANS, Spitzner) To move forward as a nation and be able to continue building a formidable cybersecurity workforce, we must turn a keen eye on ways in which a variety of lived experiences, from the board room to customer service, becomes the rule and no longer the exception.
Competency Framework = Soft Skills
Before we dive into some non-technical cybersecurity career paths, let’s first take a look at the NICE Competency Framework. How does this framework apply to filling cybersecurity job positions, especially non-technical work roles?
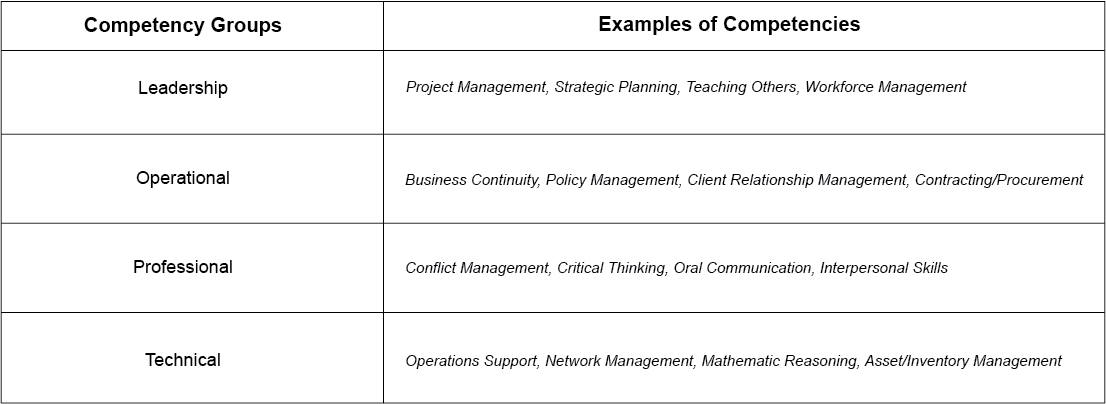
There’s a lot of discourse surrounding “competency”, not to be confused with competence. “Competencies effectively explain how an individual’s behaviors bring about the desired results in their role. As with skills, there are various types of competencies – including core competencies, which are those that any successful employee requires to rise through an organization.” (HAYS, McNeill) The core competencies, a.k.a. Competency Groups of NICE, and examples of their associated competencies, are below:
In contrast to the NICE Workforce Framework, which includes thousands of KSAs that are required to perform a specific task relative to a specific work role, the Competency Framework defines soft skills that are valuable and required for many non-technical cybersecurity positions. Similarly, the 52 work roles that the NICE Workforce Framework outlines, are not directly aligned to the Competency Framework, leaving many unidentified, non-technical and hybrid roles to be explored.
In-Demand Non-Technical Work Roles
Program Manager
Leads, coordinates, communicates, integrates, and is accountable for the overall success of the program, ensuring alignment with agency or enterprise priorities.
If anyone in the cybersecurity industry can monetize, strategize, analyze, and incentivize it is the Program Manager. They exude business, leadership, communication, organizational, and interpersonal skills. Individuals with a previous background in business, government, military, or non-profit organizations would be great candidates for this particular work role. Managers from various other industries, like retail, food, and entertainment, would all do well in such a role. To succeed, extensive knowledge of the cybersecurity threat, risk, and vulnerability landscape is required. An interest in the federal government’s research, resources, and a greater understanding of the infrastructure is also necessary.
Privacy Officer/Privacy Compliance Manager
Develops and oversees privacy compliance program and privacy program staff, supporting privacy compliance, governance/policy, and incident response needs of privacy and security executives and their teams.
Finance, healthcare, law enforcement, and education sectors are all in need of privacy officers, and there are already many jobs that exist in those sectors that serve as clear pathways of transition to this work role. There’s a lot of pressure surrounding compliance within organizations, making this a great job for people who like to negotiate and most importantly, can take a stance not easily faltered. If you don’t care what people think about you on a daily basis, and can mediate conflict, this might be a viable career path for you. Professionals funneled into this work role may come from health information management backgrounds, or even higher education professions. Extensive knowledge of privacy laws, compliance regulations, and implementation processes are necessary.
Product Support Manager
Manages the package of support functions required to field and maintain the readiness and operational capability of systems and components.
Like many managerial positions, attitude matters. Product support managers come from a wild array of backgrounds, including teachers, military, web developers, engineers, designers, business majors and more. It is a work role that benefits from being open to unconventional backgrounds that bring diverse insights and perspectives. While a deep understanding of the industry and some technical knowledge is necessary, embodying leadership is key in this role. Technical skills can be developed and improved overtime. Having a team-oriented spirit, along with a passion for cybersecurity and customer satisfaction contributes greatly to the overall success of an organization.
IT Program Auditor
Conducts evaluations of an IT program or its individual components to determine compliance with published standards.
Extensive knowledge of IT systems, infrastructure, applications, policies, and compliance regulations are all attributed to the IT Program Auditor. Individuals interested in this work role may come from an accounting background, or another profession that requires a flair for meticulousness, organization, and constant work researching, gathering, and evaluating data. Another hallmark of this profession is an affinity for multi-tasking, a determinable factor when meeting deadlines on a constant basis.
Cyber Legal Advisor
Provides legal advice and recommendations on relevant topics related to cyber law.
Many sources cite cautionary tales about cyber legal advisors, whose cybersecurity expertise claims were not up to snuff. That being said, law students interested in making a career out of advising and litigating on behalf of cybersecurity startups and corporate companies must have ample industry knowledge, a deep understanding of all cybersecurity processes, and the desire to actively keep up with the fast-paced landscape of current events. Outside of legal/advisory qualifications, highly inquisitive and motivated individuals would do well in this role, possibly even gaining an IT certification or two. There is no sugar-coating on just how determined and fully invested in cybersecurity a candidate must be to fulfill this role.
Where You Fit in the Cyber Ecosystem
Choosing cybersecurity as a career path is an admirable pursuit. With soft skills gained from previous work and/or lived experiences, there’s no reason not to consider how you could make an impact in the cyber ecosystem. Many career paths in cybersecurity, technical and non-technical, lead to high-paying salaries the further up the ladder you climb. Whether you are thinking about switching careers, or have already begun acquiring required competencies and/or KSAs, CyberKnights provides cybersecurity practitioners and job seekers a Career Journey Map, where you can map out your path, beginning-to-end. Keep in mind, you do not need to come from an IT or cybersecurity background to break into this industry. If you’re interested in seeing what soft skills you already possess, and want to start building KSAs for your resume, register here to get started. CyberKnights can help employers identify current employees with the ‘lived experiences’ that qualify them for positions. Studies have shown this career interest in employees help increase retention!